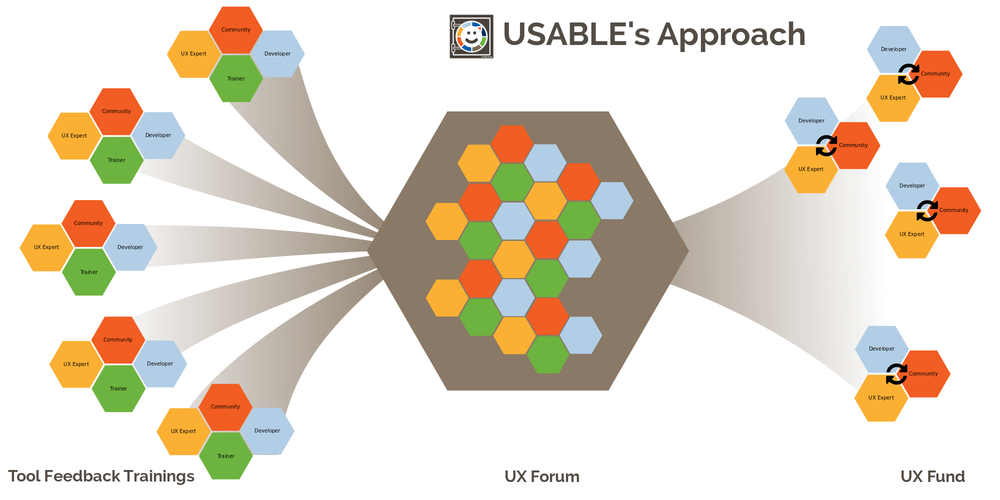
-
Announcing New USABLE Personas
Through a series of regional User Experience (UX) Workshops, the USABLE project is enhancing digital security trainers’ understanding of specific usability roadblocks that hinder adoption of important security practices for the highest risk groups across the globe and how to capture and articulate these challenges to tool developers.
 Personas, or general profiles or snapshots of end users, play an important role in the design process and allow developers (who are largely male and based in the U.S. and Europe) to better understand the needs and use-cases for their products in some of the most challenging environments in the world. Too often developers in the open source community rely on assumptions from their respective locations and experiences, which is dramatically different from the lived experiences of high-risk groups using their products. Whether they are designing for a human rights activist in China or a journalist reporting on the frontlines in Crimea, for developers to design products that are useful and usable, they must better understand who their users are, their motivations, and willingness to adopt such important security tools.
Personas, or general profiles or snapshots of end users, play an important role in the design process and allow developers (who are largely male and based in the U.S. and Europe) to better understand the needs and use-cases for their products in some of the most challenging environments in the world. Too often developers in the open source community rely on assumptions from their respective locations and experiences, which is dramatically different from the lived experiences of high-risk groups using their products. Whether they are designing for a human rights activist in China or a journalist reporting on the frontlines in Crimea, for developers to design products that are useful and usable, they must better understand who their users are, their motivations, and willingness to adopt such important security tools. During the five regional UX Workshops, trainers learned how to create and use personas to communicate with tool developers. These personas include a brief description of the user, along with a summary of their goals, strengths, and threats they face. It also includes questions from the user about specific tools or security concerns, giving the developer insight into the users’ mental model around security in general.
During the five regional UX Workshops, trainers learned how to create and use personas to communicate with tool developers. These personas include a brief description of the user, along with a summary of their goals, strengths, and threats they face. It also includes questions from the user about specific tools or security concerns, giving the developer insight into the users’ mental model around security in general. Trainers were also given time during the workshop to create their own personas based on specific communities with whom they are working. Following the workshops, the USABLE team worked with several of the trainers to finalize their personas and format them for publication. 6 personas from Southeast Asia, 5 from Europe and Eurasia, 4 from the Middle East and Northern Africa, 3 from Sub-Saharan Africa, and 3 from Latin America were published and are now available at usable.tools/personas.
Trainers were also given time during the workshop to create their own personas based on specific communities with whom they are working. Following the workshops, the USABLE team worked with several of the trainers to finalize their personas and format them for publication. 6 personas from Southeast Asia, 5 from Europe and Eurasia, 4 from the Middle East and Northern Africa, 3 from Sub-Saharan Africa, and 3 from Latin America were published and are now available at usable.tools/personas.From LGBTQI advocates to journalists, these personas capture a variety of user backgrounds, experiences, and needs. The goal is that developers will be able to use these personas to better understand the individuals using their tools, and will then be positioned to make more informed design choices that ultimately make tools more secure and accessible for high-risk users.
-
USABLE at RightsCon Toronto
In response to the emerging security and privacy concerns in product and user experience design, we would like to invite you to the UX/Tech Meetup at RightsCon Toronto on behalf of Internews and Access Now.
This meetup will be on Thursday, May 17th, 2018 from 1:20pm to 2:20pm in Demo Room.
Our theme for the meetup is how technologies can better protect people’s digital rights with user research and strategic design thinking. We are hoping to connect talents across sectors, share experience and lessons from existing projects, and combine efforts and identify collaboration opportunities. If you have any ideas you would like to share or topics to discuss, you are more than welcome to bring them to the meetup.
-
USABLE at the Internet Freedom Festival
The USABLE team is excited to be gearing up for the Internet Freedom Festival this year to contiue sharing lessons learned by developers looking to listen and engage with their users. Internews will be co-hosting the session with web accessibility expert, Nancy Reyes of HearColors Mexico, to talk about the biggest takeaways developers are learning as they continue with user-testing and exploring different ways to engage with their target users, how they are turning user feedback into concrete usability improvements, as well as the intersectionality of usability and accessibility and why it’s important. The conversation will be led by our UXFund grantees, including Mailvelope, Benetech, Peerio, Operator Foundation, and Least Authority.
The session, Usable and Accessible Security – Lessons Learned by Engaging with Users, will be on Monday (March-6) from 5:00 - 6:00pm in the Attic at the IFF venue.
Hope to see you all there!
-
Announcing the UXFund Results!
The USABLE team is proud to announce the UXFund results for the small, but targeted usability enhancement grants. Many great proposals were received and, after a thorough review process, five organizations for short-term awards were selected. A core component of all grants will be to more directly engage and listen to users, so tool creators can better understand and implement usability improvements that are needed from high-risk communities across the globe.
Profiles of the UXFund grantees can be found below:
 Mailvelope – https://www.mailvelope.com
Mailvelope is a free browser plugin for Chrome and Firefox that enables end-to-end encryption that integrates directly with your web-based mail provider, whether you are using Gmail, Yahoo! Mail, or Microsoft webmail. Mailvelope is an open-source project currently hosted on github (https://github.com/mailvelope/mailvelope).
Mailvelope – https://www.mailvelope.com
Mailvelope is a free browser plugin for Chrome and Firefox that enables end-to-end encryption that integrates directly with your web-based mail provider, whether you are using Gmail, Yahoo! Mail, or Microsoft webmail. Mailvelope is an open-source project currently hosted on github (https://github.com/mailvelope/mailvelope). Martus (product of Benetech) – https://martus.org
Martus is a free, open source, secure information collection and management tool that empowers human rights activists to effectively collect, store and transfer potentially sensitive information. Martus enables more secure information management and backups for groups and individuals across the globe.
Martus (product of Benetech) – https://martus.org
Martus is a free, open source, secure information collection and management tool that empowers human rights activists to effectively collect, store and transfer potentially sensitive information. Martus enables more secure information management and backups for groups and individuals across the globe. Peerio – https://www.peerio.com
Peerio is an end-to-end encrypted communication client that works on both desktop and mobile phone. The client allows users to setup an account for free, with paid premium versions. Peerio is an open-source project currently hosted on github (https://github.com/PeerioTechnologies/peerio-client).
Peerio – https://www.peerio.com
Peerio is an end-to-end encrypted communication client that works on both desktop and mobile phone. The client allows users to setup an account for free, with paid premium versions. Peerio is an open-source project currently hosted on github (https://github.com/PeerioTechnologies/peerio-client). Postcard (product of Operator Foundation) – http://operatorfoundation.org
Postcard is an open-source and free encrypted email client with a simple user-interface for maximum ease-of-use. Postcard is free and open-source and is currently hosted on github (https://github.com/OperatorFoundation/Postcard).
Postcard (product of Operator Foundation) – http://operatorfoundation.org
Postcard is an open-source and free encrypted email client with a simple user-interface for maximum ease-of-use. Postcard is free and open-source and is currently hosted on github (https://github.com/OperatorFoundation/Postcard).Gridsync (product of Least Authority) – https://leastauthority.com Gridsync aims to provide a cross-platform, graphical user interface for Tahoe-LAFS, the Least Authority File Store that allows for backing up local files, synchronizing directories between devices, and sharing files and storage resources with other users across all major desktop platforms (GNU/Linux, Mac OS X, and Windows). Gridsync is a free and open-source software that is hosted on github (https://github.com/gridsync/gridsync).
If you are interested in working to help any of these organizations or getting involved in supporting the USABLE project, please contact us!
-
USABLE Updates, Resources and more!
We can’t believe it’s been two months since the UXForum! To be fair, we had a lot of sleep to catch up on, and there have been some exciting staff transitions over on our team.
Going forward, Megan ([email protected]) will be leading USABLE while Jon takes on directorship of our global portfolio (including supporting USABLE!). We are also onboarding additional program support to help out.

We’ve added a massive Resources page that captures a ton of links and references from the UXForum, our reading lists, and more.
We also have some new User Personas we’ve put together from the UXForum and TFT work with our communities. These personas represent a wide variety of users of digital security tools facing a mix of threat actors.
We have created these from many common shared experiences, but for the privacy of our communities, none are 1:1 connected, and all are created from a combination of people and the work they do. The photos are public domain or Creative Commons stock photography, and the names are of course made up.
We are working with a few teams to support UX walkthroughs, accessibility, and user testing of open source digital secutrity tools! We will be focusing on our UXFund grantees first, but please ping us at [email protected] if you are a tool developer and are interested in this – and also check Open Technology Fund’s Usability Lab they run in partnership with SimplySecure.
-
Power to the Users -- From trainings to the UXForum and onwards.
Three years ago, I led a digital security training for independent media in Kyiv during the peak of the EuroMaidan protests. It didn’t go as planned.
This spring, we returned. We worked with an amazingly skilled trainer who led the local Digital Security School which had since emerged thanks to the hard work of eQualit.ie, and we brought together an amazing community of experts and practitioners who face complex challenges in their work as they dealt with the repercussions of the post-Maidan Ukrainian reality. This alone would have made for a successful training; but our goal with USABLE is to scale beyond this and get to underlying problems around tool uptake. So, we also brought a designer (who is now leading frog design’s social impact team) and a developer who led a digital security tool that the community was interested in learning more about.

Building this “Tool Feedback Training” approach to connecting high-risk users and tool developers through the training and design process, and the results we have already achieved, has been an amazing journey. It may – and should – seem simple, but the complexities of making that precise connection is far too often presumed, but not actually done. Real people facing very specific and complex security challenges become an amorphous “they.” “They” needs many things from constant, bleeding-edge security improvements to changes supporting very specific use cases; but it turns out that if you actually engage the people beyond the “they” - that you learn real, often simple, changes in user experience are the path forward.
-
UXFund: Extended to September 30!
We are extending the UXFund deadline for two more weeks - through Sep. 30! Apply Today!.
-
Yahoo!
Thanks to our friends over at Yahoo! for a great blog post outlining their amazing support of our work!
-
User Testing in Digital Security Training
During our first Tool Feedback Training, we faced some natural reluctance to “complain” about a tool being trained upon, which was magnified by the effect of having a representative from the tool in the training. To accommodate this, we leveraged the high number of facilitators during each hands-on activity to gather observational data. The trainer would set a short goal (create an account, create a record, share a record), and the participants would work in small groups to accomplish this task, with a facilitator observing each group to note where confusion or problems were occurring. To balance this with maintaining the flow of the training, the facilitators would keep each group from floundering, and the trainer would review the process for everyone before moving onwards.

-
Protecting High-Risk Tech Users: A Movement for Usability
Connecting developers with users improves tools for human rights defenders
Janvier Hakizimana has a radical idea.
“Governments and large global bodies like the United Nations subsidize new medications to fight disease. Why not also subsidize the adaptation of technology so that it can meet the needs of local communities?”
Adaptation — making tech tools more open, accessible, and customizable — matters in Janvier’s line of work. He works to support human rights defenders in the East and Horn of Africa who need secure tools to document and report human rights violations.
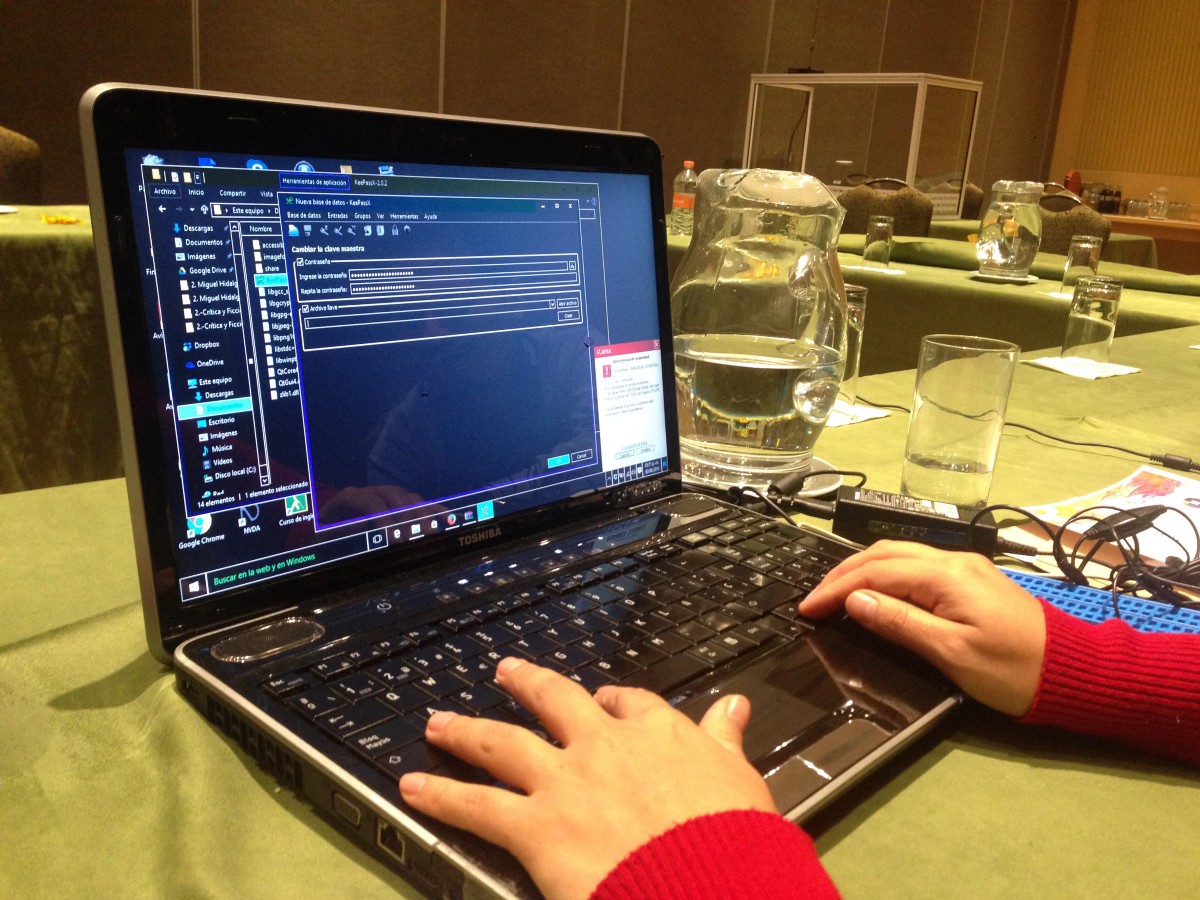 Testing the usability of secure apps through screen readers, at a USABLE training in Mexico. Credit: Mariel Garcia M
Testing the usability of secure apps through screen readers, at a USABLE training in Mexico. Credit: Mariel Garcia MWhen a tool can’t adapt to local conditions — when it is entirely reliant on an internet connection, for example, users in low-connectivity areas may not be able to use it on a broad scale.
Relying on a hodge-podge of tools that each does one thing well makes work inefficient. Worse, relying on tools that aren’t secure puts high-risk communities in danger.
Janvier supports human rights defenders, in part as a trainer for USABLE, a project designed to connect high-risk users of digital security and communications tools with the developers who make those tools, in order to make the tools usable.
Next week, USABLE will hold its first UX Forum in San Francisco, bringing digital security trainers and activists from Africa, Latin America, Eastern Europe and the Middle East with developers in the center of US tech development, for three days of hands-on collaboration. USABLE’s focus on human-centered design focuses the process on the real-world needs of activists working on sexual orientation and gender identity rights, media, democracy, and human rights in challenging and threatening environments.
-
Join us for UX in a High Risk World!
For one night only, we are opening the doors to this event!
Come meet the visionary leaders who are piloting and developing solutions for activists facing censorship, hacking, surveillance, and suppression in some of the world’s most challenging environments.
-
Where did USABLE come from?
Over at Medium, we just published What Good Are Secure Communications Tools if No One Uses Them?. This is part of the “origin story” of the USABLE project, based on a difficult digital security training during the middle of EuroMaidan.
 Ukraine’s EuroMaidan protest. Photo by Alexandra (Nessa) Gnatoush - Flickr
Ukraine’s EuroMaidan protest. Photo by Alexandra (Nessa) Gnatoush - Flickr -
Learning how to balance design and training
The USABLE team is halfway through our Tool Feedback Training process, and the first two TFTs were hugely informative. We worked with groups doing amazing work while facing widely different challenges; including censorship, targeted malware, and situations where digital security problems can become physical security ones.
One of the concerns we had going in to this process was balancing the digital security training for the participants with human-centered design exercises, which is why we spent so much time working through this during our Security and Design Workshop.
In both trainings however, the participants not only responded enthusiastically to the design exercises we conducted, but expressed ongoing interest in applying design thinking to their project work. The design-centric agenda items have actually meshed well with the digital security curricula, engaging participants in the design process, creating users personas, and supporting the tool developers in coming up with prototyped design changes. We’ll post soon on building user testing directly in to the training process.
The dSchool’s Wallet Exercise has been very useful as a short, fun way to get into the mindset of design, as it leads you through a series of thought, listening, and feedback exercises with a partner. It - along with many of the other design exercises – creates a great icebreaker effect by putting everyone on the same level as they work through a problem.
We’ve updated the TFT schedule to better reflect how these first TFTs went - you’ll see a back-and-forth between threat modeling, design exercises, and tool trainings.
-
Training and Design
At the Security and Design Workshop, we realized that our original plan of book-ending a classic digital security training with human centered design exercises was not ideal – many elements of learning and exploration that are key to training are similarly core to collaborative design.
To test this out, we spent one afternoon running a digital security training on mobile security. We based the training on the ADIDS adult-learning approach, and used a selection of Level Up curricula components, integrating human-centered design components into the flow of the training. The rest of this post will run through the components of the training and the outcomes from it.
-
Learnings from the Security and Design Workshop!
The USABLE project is built around a core commitment to listen - to users, to trainers, and to our partners. As we began assembling the team of amazing designers and usability experts we are working with, a common thread emerged around a desire to connect and frame their inputs as usability experts for the digital security space and map out how they would engage during the tool feedback trainings.
We were able to bring together a Security and Design Workshop in mid November, thanks to the amazing generosity and flexibility of our partners and hosted in ThoughtWorks’ new San Francisco offices. This gave the USABLE team a chance to go over operational security concerns for working with vulnerable populations and let the designers experience firsthand both some of the digital security tools we hope to work with, and the process of a digital security training. More importantly, however, was the chance to really dig in to our plans for integrating need-finding and human centered design into the digital security training process to create the “Tool Feedback Trainings” (TFTs) we envision.
For needfinding, USABLE is integrating core aspects of the SecondMuse’s Internet Freedom Need Finding Toolkit into this process to supplement our pre-training interview and engagement processes with our local partners and trainers. Members from the SecondMuse team were able to join us and help us work through their framework and adapt it to the Tool Feedback Training model in USABLE. This helped us discover what information is valuable to match a community with a tool developer, as well as understanding the threats and capacity of each community that goes into digital security trainings.
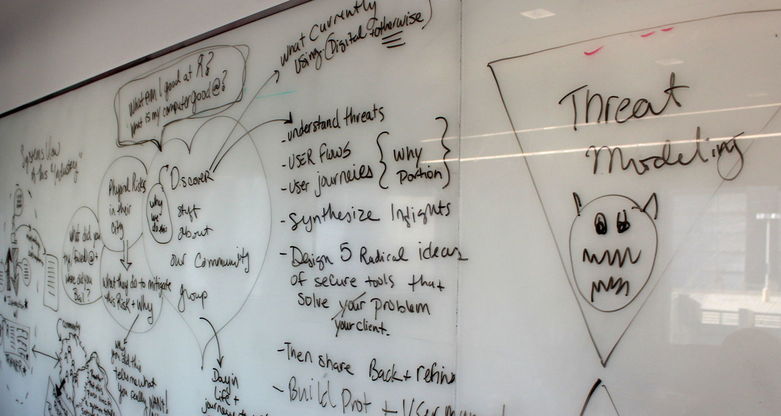
For the rest of the workshop, we worked on integrating HCD practices into the training process. The final day began with a series of human centered design exercises led by ThoughtWorks that would be adaptable for the TFT scenarios, from introductory exercises to more practical ones, such as having participants design the training or manual for a tool as a way to focus the tool’s actual interface on those aspects that truly require training, as opposed to those which could be set to secure defaults, automated, or provided as “advanced” options.
Learnings
-
Announcing USABLE!
![[☺]](/images/safe.png) We’re very excited to announce USABLE: Usable Security Apps By Leveraging End Users! USABLE, a project of Internews, brings a human centered design lens to digital security tools through a three-phase process (detailed out below) with add-on benefits of producing community-led user personas, connecting tool developers with trainers and at-risk users, and encouraging sharing of design patterns and usability challenges along the way.
We’re very excited to announce USABLE: Usable Security Apps By Leveraging End Users! USABLE, a project of Internews, brings a human centered design lens to digital security tools through a three-phase process (detailed out below) with add-on benefits of producing community-led user personas, connecting tool developers with trainers and at-risk users, and encouraging sharing of design patterns and usability challenges along the way.We’re just getting started and are locking in our first communities, and expect to be running these needs-based trainings throughout early 2016. We will be sharing the user personas and learnings from these trainings over the next few months.